CLOUD SECURITY ARCHITECTURE
The key to creating a cloud security architecture strategy, is to obtain and integrate tangible business requirements including security policies, legal and regulatory requirements into the overall strategy and map them end to end with every artefact. Of equal importance is the integration with the organisations current processes, including for example, the classification policies and risk management methodology.
Pulling all this together can be done quickly and tangibly utilising the Toolkit, which will enable you in creating a useful listing of all your key stakeholders and locations of key processes and policies and standards, bringing everything closer to your fingertips rapidly.
If the organisation has not already selected the CSP(s) or model(s), then you need to support them based on the business requirements and enterprise architecture planning.
Key Security Architecture Strategy Artefacts:
- Creation of a security architecture blueprint/HLD encompassing all security controls necessary to protect the organisations and customers assets.
- Creation and implementation of cloud security principles, standards and patterns.
- Provision of security governance through TDA and technical security evaluations/risk assessments.
- Detailed or low level designs to enable the deployment of security controls as part of an overarching security program of work, reusing or augmenting where feasible artefacts already deployed, and introducing new technology and processes where necessary.
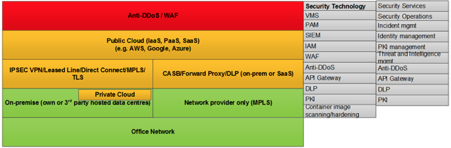
Example of HIGH LEVEL Cloud Security Architecture View:
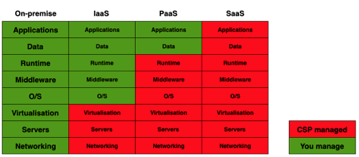
Cloud service models:
Key Security Architecture Artefacts:
- Perimeter security; CASB, Anti-DDoS, WAF, DLP, API Security
- PKI management and automation (encryption of ALL data at rest and in transit)
- Secrets management on premise (PAM) and in cloud
- Security log management (SIEM)
- Compute, Storage and Database security; endpoint protection (AV, IPS, Hardening)
- Centralised identity and access management (internal and external)
- DevSecOps and security operations integration and operability.
